Introduction
This is going to be a multi-part series of articles with the end goal of producing a solution which handles security/identity claims across domain boundaries using WCF services and Active Directory Federation Services 2.0 (with a federation trust) and Active Directory. In order to demonstrate an approach to handling claims, we need an environment which is capable of supporting the infrastructure configuration we require.
Network Design
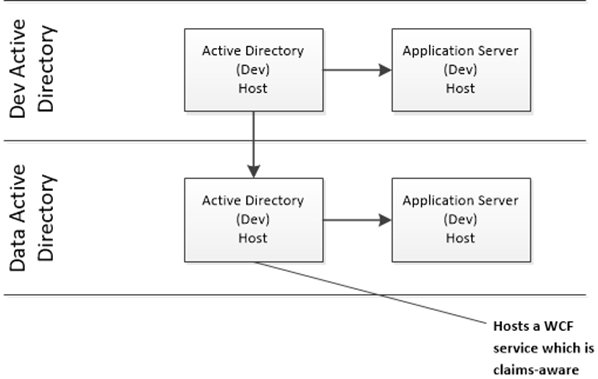
I strongly recommend that you put the time and effort into understanding the network topography. When designing a key foundation of your approach to security, it’s critical that you have a working knowledge of the kind of trust you are placing in your trusted sub-systems. For the next few articles, I’m going to rely on the following network design, which you can (not without some effort) establish for yourself using virtual machines:
Host Configuration
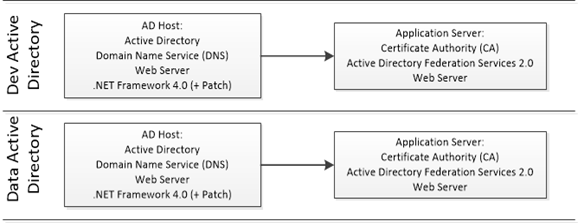
To keep resource usage to a minimum, I’ve designed my test environment to reuse hosts for key roles. In practice, you might not normally mix roles in a production environment – refer to the appropriate ‘best practices’ to properly plan your infrastructure and deployment of critical roles! Here’s a view of what is on each host:
Installation and Configuration
You’ll need a minimum of two server installs to make this happen, although I’m using four to separate ADFS 2.0 and to configure an Enterprise Certificate Authority rather than a standalone CA. You’ll also need the Windows Identity Foundation (WIF) SDK installed with your copy of Visual Studio (Visual Studio can be installed elsewhere – not on your test servers).
I’ll be using Visual Studio 2010 for this, but I’m sure there’s a solution for Visual Studio 2012. To streamline your configuration, I’ve provided links two some excellent walkthroughs on the MSDN blog site – the one you need to pay attention to is the ADFS 2.0 installation and configuration.
My Mobile Configuration
Since this is a fairly intensive number of operating systems, I’ve put together a fairly decent local configuration which I can take with me. I’m using a 480 GB SanDisk SSD in an eSATA external enclosure (my laptop does not support USB 3 at the moment). I’m running VM images off the SSD and getting very respectable performance. No problems running four VMs in parallel.
How to Get Up and Running
My best advise is to follow the links below. You’ll need a fair amount of stuff downloaded, so better jump on that. Once you have some clean OSes and the installation packages, my best advise is to follow the walkthroughs. Be careful not to accidentally skip anything, the configuration is a bit tricky at times, but if you follow the walkthrough closely you should have a working environment in about half a day or less. My configuration varies to the walkthrough (as I have two domains), but if you duplicate the configuration for two different directories you should have something which can work.
Links Galore
If you’re going to build a test environment (frankly, just do it – it’s the best way) budget at least a day to get everything configured properly. Don’t cut corners, it’ll only hurt you later.
Check back soon for the next article, where we’ll start to get familiar with the environment, and build a claims-aware application.
Important Downloads
.NET Framework 4.0 Runtime
http://www.microsoft.com/en-au/download/details.aspx?id=17718
.NET Framework 4.0.3 Update
http://www.microsoft.com/en-au/download/details.aspx?id=29053
Update 4.0.3 for Microsoft .NET Framework 4 – Design-time Update for Visual Studio 2010 SP1
http://www.microsoft.com/en-au/download/details.aspx?id=29054
Active Directory Federation Services 2.0 (RTW)
http://www.microsoft.com/en-us/download/details.aspx?id=10909&hash=Hx4OGpwvFzmf7%2bC7rR1nq18CYhcY%2bSE4ok1ifL%2fvSkYIpezfAxg6ePR2zpfAplmm6g%2fUyL1VU7RtmnuR6T4NWg%3d%3d
Windows Identity Foundation (Runtime)
http://www.microsoft.com/en-us/download/details.aspx?id=17331
Windows Identity Federation SDK
http://www.microsoft.com/en-us/download/details.aspx?id=4451
Installation and Configuration Walkthroughs
ADFS 2.0 Installation Walkthrough
http://blogs.msdn.com/b/alextch/archive/2011/06/27/installing-a-stand-along-adfs-service.aspx
Establishing a Federation Trust Walkthrough
http://blogs.msdn.com/b/alextch/archive/2011/06/27/establish-federation-trust.aspx
Building a Claims-aware Web Application Walkthrough
http://blogs.msdn.com/b/alextch/archive/2011/06/27/building-a-test-claims-aware-asp-net-application-and-integrating-it-with-adfs-2-0-security-token-service-sts.aspx
These walkthroughs really helped!
Finally.. If you hit problems with your STS certificate – check the HTTPS bindings of your local IIS:
http://www.shutuplaura.com/journal/2010/1/5/adfsv2-rc-iis-certificates.html