Well-Architected for Security: Advanced Session : Level 300
Ankush Chowdhary, Head of Security, Risk and Compliance, Professional Services, Amazon Web Services
** Note: These are notes taken from various sessions and the keynote of the 2017 AWS Public Sector Summit held in Canberra, Australia. The information might be slightly unstructured, and the photos might be a bit raw.
Note: The level 300 sessions were being squashed into short sessions, as a consequence the presenters were really under some pressure to zoom through the content. As a result, I found it difficult to make notes and listen at the same time in an effective manner.
Well Architected for Security
Design principles
* Security at all layers
* Visibility and traceability
* Least privilege (need/time)
* Data centric (security stays with data)
* Security by design (automation, policy)

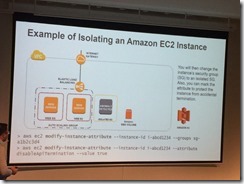
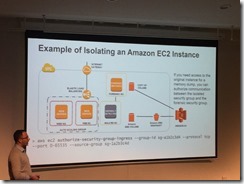
Identify security boundaries
InfoSec controls defined
System hygiene (patching, management)
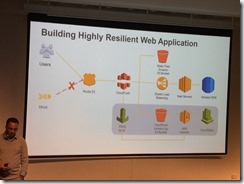
Weight or latency based routing
CloudFront implements geo rules
CDN + WAF helps traffic analysis
DDoS Shield service (pro service)
Scale out triggers on DDoS. Evaluate legitimate users,
Web Application Security
Cloud formation template – builds WAF profile (no code)
OWASP Top 20
* insufficient attack protection
* WAF can cater for this
* Can identify vulnerabilities
* Buy time to develop patch
* WAF can implement temp patch (web ACLs) if you know the attack vector
Data Centric


Classification of data (at creation)

Hybrid data storage
Server side encryption
Can be policy driven
Can use 2FA/MFA device
Integrity must be maintained
Availability must stay consistent
Secure at rest

Use policies to enforce security

Don’t use master keys
Enforce by policy
KMS integrated
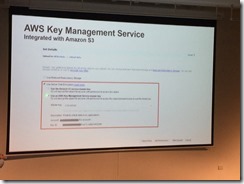
Built into the platform. Key management by platform.
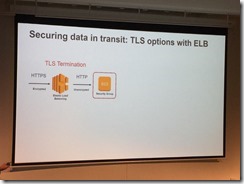
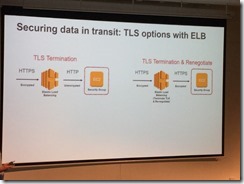
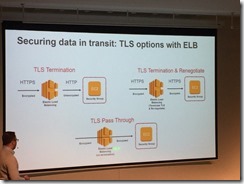
Use TLS TERMINATION
Usually to NLB

CloudFront – BYO domain & cert
SNI is cheaper
Old software doesn’t support it
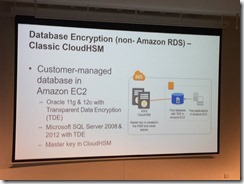
CloudHSM
Key management (no AWS access)

New v2
Used for document signing, Etc

No upfront payment
Built in HA
Console access
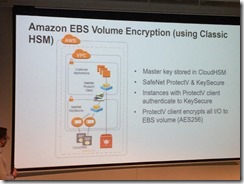
EBS volumes encrypted
Requires 3rd party software
Complex. Requires Classic
Identity

Policy, policy, policy
Resource tagging
Force tags to regions

Can be used in security automation
Function based too
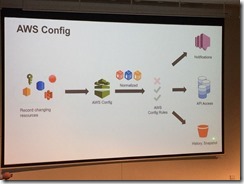
Automating compliance

One option… use resource relationships
Check status of compliance
Use lambda:
Examples
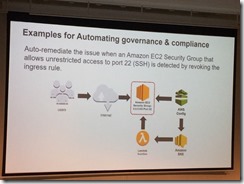
Config rules trigger on change
Lambda can automatically respond

New: from management console
Rule repository available