This is a two-part series of posts.
The first day covered Modules 1 & 2, and the second day, Modules 3 & 4.
Owing to the pace of the training, I only managed screen shots and sporadic notes.
The Q&A section is the most rewarding, I’ve added them at the end.
Module 3
Federation
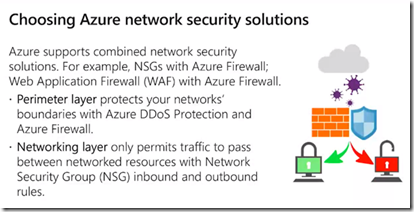
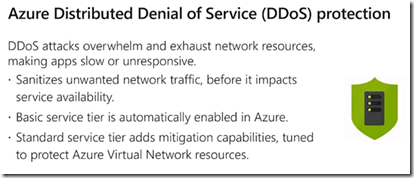
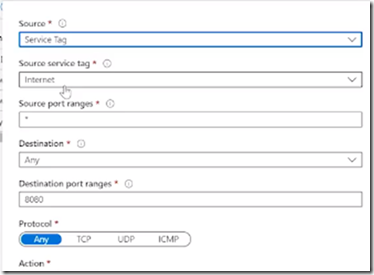
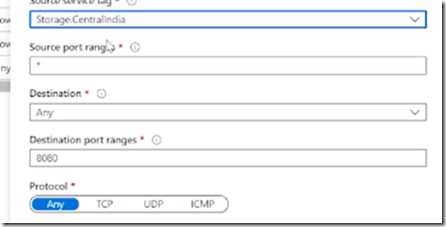
Network Security Groups
Priority of rule (low to high) determines which rule applies (when they conflict)
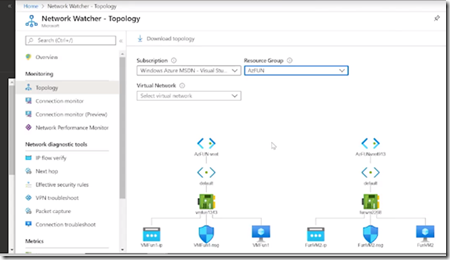
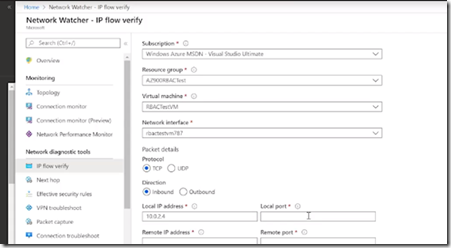
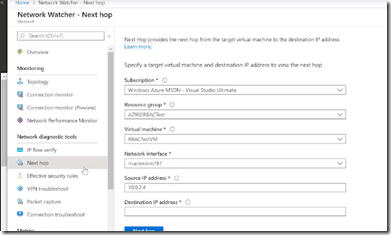
Network Watcher
Topology
IP Flow
Next Hop
Default rules can’t be removed (deny all)
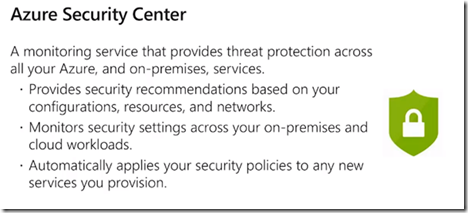
Azure Security Center
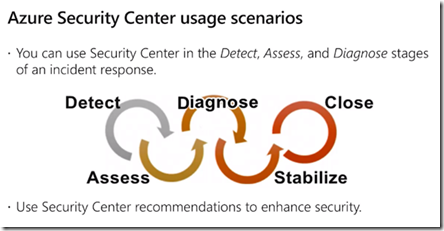
Incident Response Tools
Key Locker/Key Vault
Can get keys via API
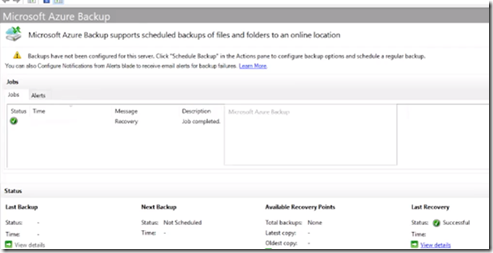
Azure Backup
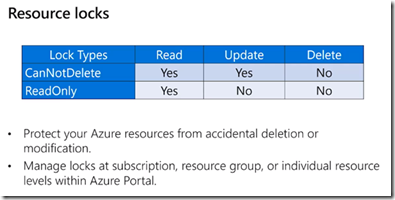
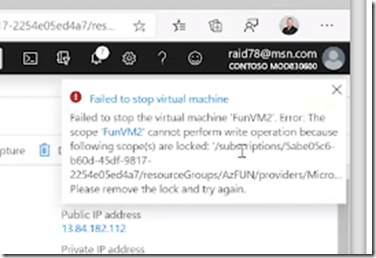
Resource Locks
Update lock coming
Read Only Lock prevents changes to AZ resource PROPERTIES (like stopping a VM)
Lock chains to all dependencies as well (inheritance)
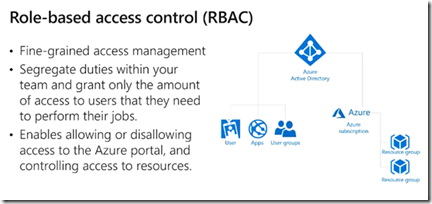
Alternatives to Resource Lock: RBAC, policy
Blueprints
BILLING
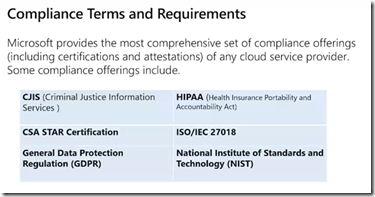
Trust Center
Trust centre
https://www.microsoft.com/en-us/trust-center
Questions & Answers
Is Virtual Machine Disk space is part of Azure File storage internally?
Disk storage and file storage are separate services but they all fall under Azure storage: https://docs.microsoft.com/en-us/azure/storage/common/storage-account-overview.
What role does Active Directory Federation Services play between AD DS and AAD?
It can provide SSO services for both your local AD instance and your AAD instance. It unifies the authentication for both instances behind one identity, thereby providing an advantage for using ADFS.
How is the data protected if azure can talk with AWS? How secure is it when it talks with AWS?
Most of Azure’s data and storage services either offer encryption out-of-the-box or supports encryption. You can find an overview here: https://docs.microsoft.com/en-us/azure/security/fundamentals/encryption-overview. Now, to connect an external network to Azure, typically you can use Azure VPN Gateway to do so. VPN Gateway will encrypt all your communication going in and out of your Azure networks. More on VPN Gateway: https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-about-vpngateways.
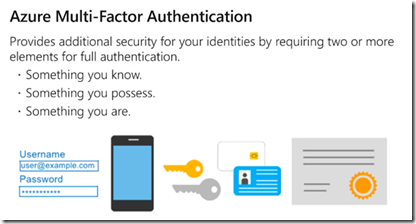
What if we lose password in multi factor? How do we get that sorted?
You would typically contact your administrator to reset it, or take a look at https://docs.microsoft.com/en-us/azure/active-directory/user-help/multi-factor-authentication-end-user-app-passwords.
So, in Azure Firewall it’s Priority-based (first application is resulting rule) and is NOT like GPOs where last applied sticks?
Correct, you can find out how Azure Firewall processes its rule logic here: https://docs.microsoft.com/en-us/azure/firewall/rule-processing.
why priority number ranges from 100 to 4096?
There is a limit to the number of rules per NSG you can create.
rules in Azure is a bit similar with ACL then?
Yes they are similar.
If you get a lot of denys on a network rule, can you set a notification to say an email or a teams channel?
You can use a combination of Network Watcher and Azure Monitor to monitor your network services.
Built-in Azure KeyVault, yes please! Can this be used for external non-Azure applications ? Assume it would rely on AzureAD/ADFS?
You could do, AKV is a stand-alone service as well. More info on: https://docs.microsoft.com/en-us/azure/key-vault/.
Keyvault looks really clunky compared to things like 1password…. why?
Azure Key Vault is more than just a password manager. You can read more on AKV at https://docs.microsoft.com/en-us/azure/key-vault/general/overview.
is AIP default enabled for all customers?
No, you can manually or automatically apply labels: https://docs.microsoft.com/en-us/azure/information-protection/what-is-information-protection.
what is the difference between Azure ATP vs Defender ATP?
Azure ATP monitors the traffic on your domain controllers. Microsoft Defender ATP monitors your endpoints and provides a single interface you can use to protect your environment.
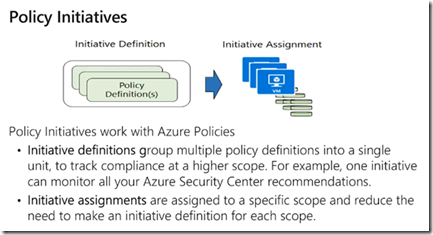
Initiative = collection of policies
What is different bet Policy and Protection Rules
Azure Policy allows you to enforce compliance on your Azure resources. Rules allows you to block or grant access to certain IP addresses, ports, or URLs.
Resource group scope
Can the policies be applied to specific group of users? like only admin group can create VMs but not others?
You can use RBAC to do so and assign a group of users the same VM role.
What can the contributor do in IAM Access?
Grants full access to manage all resources, but does not allow you to assign roles in Azure RBAC.
can we group/tag our AKV?
You can add tags to any Azure resources you need.
Will the CanNotDelete lock apply even as full admin / owner?
Yes, it applies to everyone because the lock is on the resource itself.
any reference to do the tagging in AKV?
Try: https://docs.microsoft.com/en-us/azure/azure-resource-manager/management/tag-resources
For a resource with a read-only lock, will auto-shutdown still work?
A read-only lock on a virtual machine will prevent all users from starting or restarting the virtual machine.
Will the CanNotDelete lock apply even as full admin / owner?
Yes, it applies to everyone because the lock is on the resource itself.
any reference to do the tagging in AKV?
Try: https://docs.microsoft.com/en-us/azure/azure-resource-manager/management/tag-resources
For a resource with a read-only lock, will auto-shutdown still work?
A read-only lock on a virtual machine will prevent all users from starting or restarting the virtual machine.
can you login and reboot by cmd line if read only lock in on
A read-only lock on a virtual machine will prevent all users from starting or restarting the virtual machine.
Recently I had issues with locks when using Azure migrate – I was only able to perform the initial replication after being granted User Access Administrator in addition to contributor – Why is that?
You should remove all locks if you are doing a migration. Locks are only used once you have everything set up and you do not want any accidental modification or deletion to occur.
How can I enforce tagging to be mandatory?
Yes with Azure Policy.
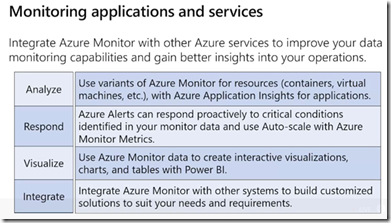
Did I see that I can connect Azure Monitor to my on-prem environment?
Yes, you can hook your on-premises machine logs into Azure Monitor as well: https://docs.microsoft.com/en-us/azure/azure-monitor/overview.
Can I use Azure Policy talk to Azure Monitor to shut down VMs that are running slow code?
Depends on the type of logs that can be collected from your on-premises environment but yes, you can define those specific log queries in log analytics.
how does the monitor differ with Azure ATP (from security monitoring perspective)?
Azure Advanced Threat Protection (ATP) is a cloud-based security solution that leverages your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization. While Azure Monitor maximizes the availability and performance of your applications and services by delivering a comprehensive solution for collecting, analyzing, and acting on telemetry from your cloud and on-premises environments. It helps you understand how your applications are performing and proactively identifies issues affecting them and the resources they depend on.
OT: What’s the conventionally official way to pronounce “Azure”? Ah-zure or Ashure?
Either is fine – depending on which pronunciation you are more comfortable with.
How many types of locks are available ?
Two – ReadOnly and DoNotDelete.
Is there someone I could talk to about how to handle ITAR *outside the US*, based on the US State Department’s recent “encryption carve out” determination?
It’s best to have a chat to the Azure Support team for specific queries like this, as the documentation for compliance may not cover every case. Submitting a support request via the portal and detailing your request will get you in contact with a support engineer who can help you through this process.
I assume Compliance Manager is only based on MICROSOFT compliances, not based on what is then built / is on top of Azure, correct?
Compliance Manager can be used to check your compliance when using Azure products and services: https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-manager-setup?view=o365-worldwide.
sorry whats the difference between stateful and stateless in APIs in App Services and Service Fabric
You might find this a useful read: https://www.geeksforgeeks.org/difference-between-stateless-and-stateful-protocol/.
Whats the Blueprint again?
Azure Blueprints enables cloud architects and central information technology groups to define a repeatable set of Azure resources that implements and adheres to an organization’s standards, patterns, and requirements. Azure Blueprints makes it possible for development teams to rapidly build and stand up new environments with trust they’re building within organizational compliance with a set of built-in components, such as networking, to speed up development and delivery.
Difference between blueprint and template in VMs
Azure Blueprints contains many artefacts, of one of them are ARM templates
what is the disadvantages of moving it?
To move any resource between regions involves a full re-deployment of the service.
So Licensing for virtual machines is practically a lease as long as the VM resource is still on? Is the OS license a recurrent and perpetually charged cost?
Virtual machines are PAYG so you can start it up and shut it down whenever you need it unless you purchase a VM through a reserved instance.
Do we get told before Azure take back the low priority servers?
Yes, you do get a brief notice.
DO you have R embedded in AZURE?
Some of our services supports R.
Microsoft certifications open new opportunities, and pathways to make greater impact.
Don’t forget to take up the free discount for the AZ-900 certification post this event.
Can I have my free trial subscription and a paid subscription simultaneously linked to my same @outlook.com account?
Yes, they will just be two separate subscriptions.
is there free options to us VM?
No, there is no free tiers for VMs.
Can we downgrade as well if we have 3 year reserved?
You will end up paying an exiting fee so make sure you do want an RI before you commit