Welcome, 2015 – may you be an improvement on your predecessor.
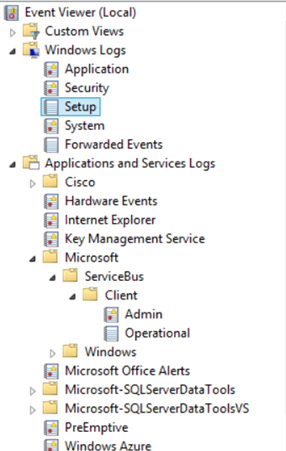
Today’s article focuses on the deceptively non-trivial task of reading from the Windows Event Logs using the Microsoft .NET Framework. For those who haven’t looked there in a while, here’s a quick look at the Event Viewer:
Now there are the usual suspects like the Application, Security and System logs of course, but on more recent editions of Windows, you might make note of the category beneath the standard “Windows Logs”, namely “Applications and Services Logs”. We can read from those as well as the standard logs.
Windows Event Log Tree
My Scenario – Viewing Log File Content
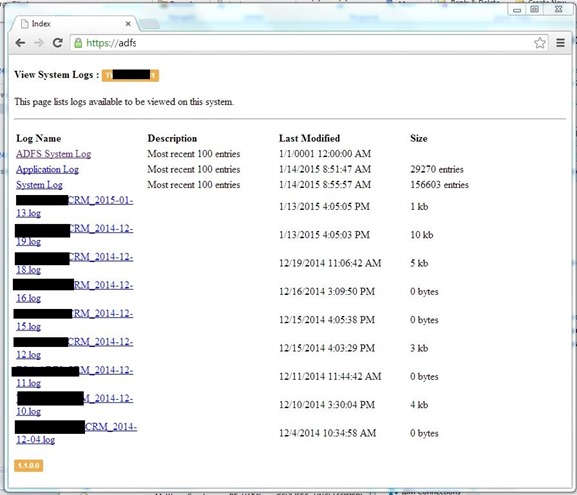
At the moment, we don’t have a logging approach which consolidates system logs and rolling log files into a single location. While we are waiting for that capability, I decided to quickly roll an ASP.NET MVC site which would effectively publish the content of local log files for remote users to view without the hassle of having to log on or RDP to the machine.
The “Log View” web application needed to do the following:
- Through configuration, read log files contained in (one to many) specified local directories
- Through configuration, read (one or more) log files based on a specific path/filename
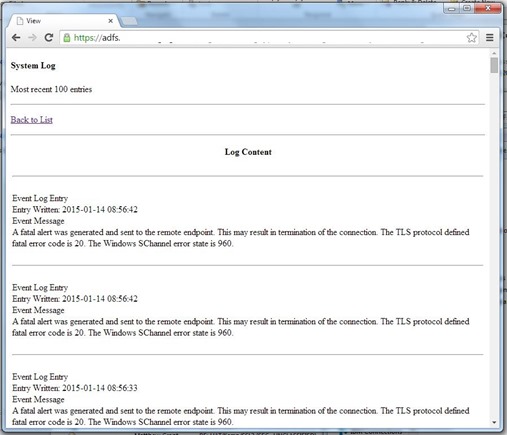
- Read the Security, System and Application system logs, displaying the most recent 100 entries
- Through configuration, read the AD FS admin log when installed on an AD FS server
- Allow anonymous authentication
This web application is meant for development/test environments, hence the anonymous authentication requirement.
Different Approaches – Reading Logs
The standard Windows Logs – a well beaten path – have special support in the .NET Framework. Provided you have the appropriate permissions, reading log entries is relatively straightforward:
var eventLogItem = System.Diagnostics.EventLog(“Application”);
var numberOfItems = eventLogItem.Entries.Count;
Of course, reading from the log is just as simple:
foreach (EventLogEntry entry in eventLogItem.Entries)
{
// read the individual event
}
You don’t (seem) to require any special permissions as a local user to read from the Application and System logs, a standard user account seems to have read permissions by default – even on Windows Server 2012 R2. This does not apply to the Security log, which would seem to require special permissions or policy – see more on this below.
However, things change when you want to read from a non-standard system log. In my case, I wished to read from the AD FS/Admin log on a Windows Server 2012 R2 machine which had the Active Directory Federation Services (AD FS 3.0) role installed.
Reading Non-system Logs
Once we veer away from the standard ‘System’ and ‘Application’ logs, the implementation gets a tad trickier – and more brittle in terms of functionality. You have to abandon the friendly EventLog class and instead have to use the EventLogQuery class, as below:
string LogName = “AD FS/Admin”;
var query = new EventLogQuery(LogName, PathType.LogName, “*[System/Level=2]”);
query.ReverseDirection = true;
Note that “log name” seems to need to match the “path” of the log if it resides under subfolders in the “Applications and Services Logs” section. Note that I’ve used the “ReverseDirection” property to show the most recent log files first. To actually read entries from the log, you invoke the tastefully named EventLogReader class, like so:
using (var reader = new EventLogReader(query))
{
// implementation here
}
You might be wondering how one would consume the EventLogReader? Happily, I can provide you with the implementation I’ve put together for my AD FS log reader:
var sb = new StringBuilder();
for (EventRecord eventInstance = logReader.ReadEvent();
null != eventInstance; eventInstance = logReader.ReadEvent())
{
sb.AppendLine(“<hr/>”);
sb.AppendFormat(“Event ID: {0}<br/>”, eventInstance.Id);
sb.AppendFormat(“Publisher: {0}<br/>”, eventInstance.ProviderName);
sb.AppendFormat(“Time Created: {0}<br/>”, eventInstance.TimeCreated.Value);
try
{
sb.AppendFormat(“Description: {0}<br/>”, eventInstance.FormatDescription());
}
catch (EventLogException e)
{
// The event description contains parameters, and no parameters were
// passed to the FormatDescription method, so an exception is thrown.
sb.AppendFormat(“EventLogException: {0}”, e.Message);
}
}
There are obviously more properties available, don’t limit yourself to what I’ve included above. Also note that it’s possible to have an exception thrown when invoking the FormatDescription() function – it’s worth catching unless you want your logic to die when it can be reasonably anticipated.
Errors at Runtime
The first few times i deployed and ran my web application, I encountered some nasty exceptions being thrown. I was running with the default ApplicationPool identity, which I decided I needed to replace with a dedicated local user. I created a local user called ‘svc_adfs_logs’ and made it a member of the local IIS_IUSRS group as well as making it the identity of my web application’s application pool.
The errors occurred when accessing the Security and the AD FS logs. I had to dig deeper.
Permissions and Settings
This is where things get interesting – aside from the standard System and Application logs, pretty much every other log I tried to read from, I’d encounter a permissions – or registry – issue.
File Permissions (ACLS)
One place to check are file permissions themselves. The logs are files residing under the Windows directory (by default) which is usually this path: C:\Windows\System32\winevt\Logs
If you’re unsure,in Event Viewer, just right click on the log name and select properties:
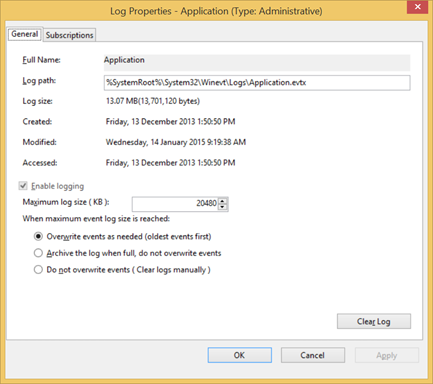
Log Properties in Event Viewer
In my case, I assigned basic read access to the app pool identity of my web application:
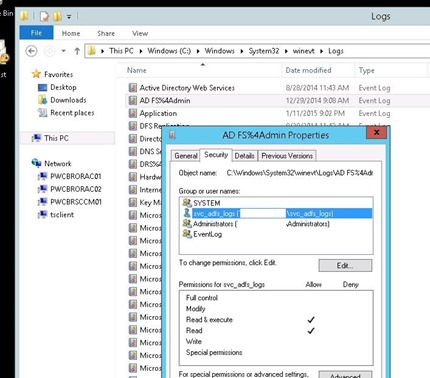
Assigning read access to the web application identity
Group Membership
The next obvious step is to ensure that your process’s identity (the account which the application is running under) is a member of a local, built-in security group called (aptly) ‘Event Log Readers’. You administer this membership via the local Groups in Computer Management:
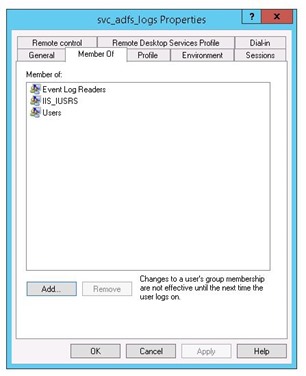
Ensure your application’s identity/account is a member of the ‘Event Log Readers’ group
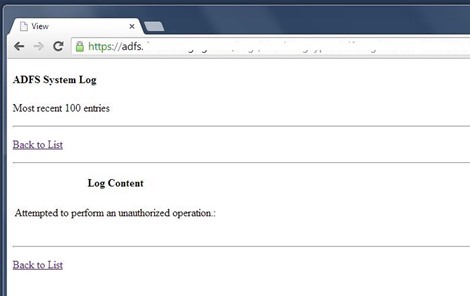
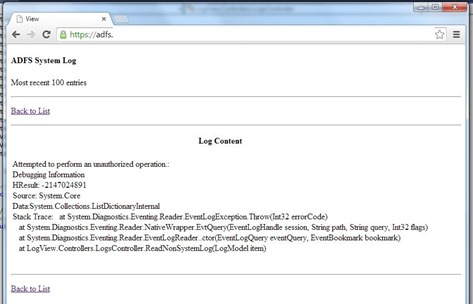
Which should resolve the following exception (if you encounter it):
Attempted to perform an unauthorized operation.
at System.Diagnostics.Eventing.Reader.EventLogException.Throw(Int32 errorCode) at System.Diagnostics.Eventing.Reader.NativeWrapper.EvtQuery(EventLogHandle session, String path, String query, Int32 flags) at System.Diagnostics.Eventing.Reader.EventLogReader..ctor(EventLogQuery eventQuery, EventBookmark bookmark) at LogView.Controllers.LogsController.ReadNonSystemLog(LogModel item)
Summary
Well, aside from writing some pretty simple boiler plate code, it was really quite easy to put together a well articulated log file viewing web application. I may consider publishing the source for this web application at a later time, once I’ve cleaned up the implementation a little bit (it’s a bit messy).
You should never be assigning local Administration rights when reading or writing to system logs – it’s worth the time investigating permissions and policies before going to those kinds of extremes.
There was one last avenue which I was exploring which involved setting SDDLs in the registry, but it turns out this was not necessary. I’ve included the links though in case you’d like to find out more.
Further Reading/References
Basic “how to” query event messages – http://msdn.microsoft.com/en-us/library/bb671200(v=vs.110).aspx
Permissions to read event logs – http://geekswithblogs.net/TimH/archive/2005/10/05/56029.aspx
How to set event log security – http://support.microsoft.com/kb/323076
Which leads us to….
Introduction to SDDL – http://msdn.microsoft.com/en-us/library/aa379570.aspx
The file ACL trick to get an SDDL: http://stackoverflow.com/questions/9907510/is-there-a-tool-to-generate-sddl-security-descriptor-definition-language-strin

![[MiniProject] Part 2: The Refactor](https://sanderstechnology.net/wp-content/themes/customizr/assets/front/img/thumb-standard-empty.png)