Introduction
There’s no doubt that we are living in a highly connected era, partially driven by an ever expanding consumption model where technology is sustained by a growing list of different models and service providers. The established, old world, architecture which used to define a monolithic corporate IT infrastructure is being overrun by the need to innovate and deliver solutions faster to meet the speed and tempo of modern business practices.
Naturally, you’ve probably heard this all before. You may come across vision statements like this one:
“Build a manageable framework of environments and capabilities that will support the ongoing needs and tempo of the organisation and its stakeholders.”
In the past this might have looked like one big infrastructure project, but in the era of commodity micro services and pay-as-you-go scale there are many alternatives which force a rethink.
Where the needs of the Enterprise and the advantages of the cloud often collide is around security and identity. One could argue that a service or application bereft of identity has limited uses, and so it follows that to take full advantage of on premises and cloud solutions, the identity problem must be addressed to deliver full value.
First, let’s establish a common lexicon:
–Identity provides information we know about a user,
–Authentication establishes “who” an identity is,
–Authorization determines “what” actions or activities an identity is permitted (or barred) from performing
Effective identity management is a critical foundational requirement of any Enterprise
Most Enterprises already have some degree of identity and access solutions in place. This has been a necessity for many decades as digital transformation activities have descended upon the modern workplace. We could completely reengineer for identity, but wouldn’t it be easier to integrate modern standards and tools, whilst leveraging existing investments?
Enter Identity Federation
Future-aware
–Efforts to define an Enterprise capability must consider the advances and impact of modern security patterns and practices,
–Identity management should be extensible, to allow for multiple sources of truth for identity information,
–Applications and services can have different identity consumption requirements
What if we were to harness the benefit of existing LDAP-type identity stores (such as Active Directory) and leverage a modern identity broker (such as Active Directory Federation Services) to lift and securely expose identity & authentication?
Lets take a look at how we might reframe our view of the various components. For ease, I suggest grouping existing applications into roles, as illustrated below. Broadly, we have a number of boxes to fill to see if identity federation requirements can be met:
- Authentication provider(s) – existing stores used to authenticate users,
- Identity providers – applications, data marts or services which contain user identity,
- Identity Brokers – services which expose authentication mechanisms & identity information,
- Identity Consumers – applications and services which consume authentication & authorization
Here is an example identity topology for an Enterprise with some common examples from the above categories:
Hybrid Architecture
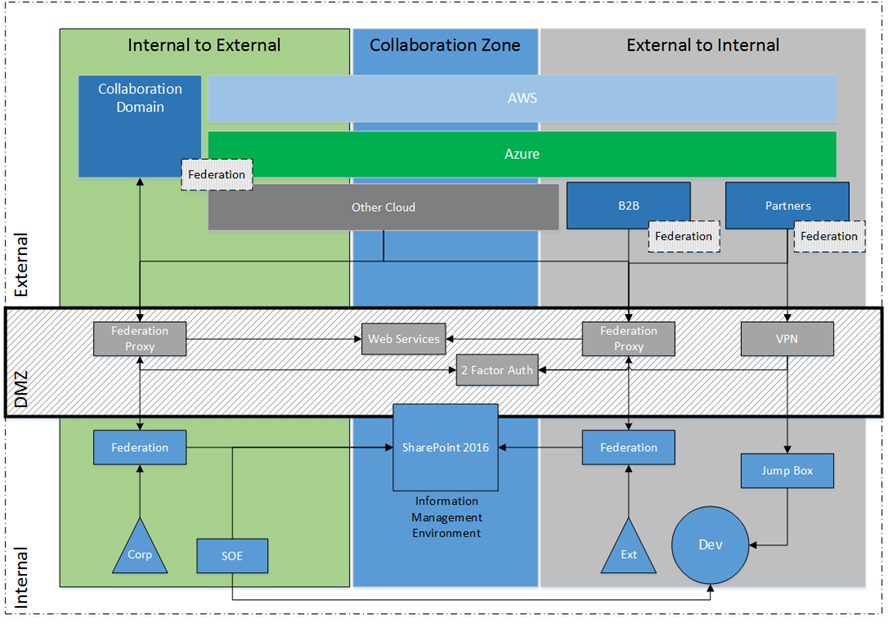
Once we have established a realistic picture, the benefits of putting together an Identity strategy become a lot clearer as well. Considering the vast array of identity-aware services and applications, it is now possible to paint a hybrid view which sustains business capability across corporate network boundaries, as depicted below.
Naturally this is still quite a simplistic – if aspirational – view. The emphasis is on the cross (domain) boundary collaboration and service consumption approach, which uses identity to create opportunistic technology benefits (e.g. cloud service consumption, B2B integration). This can work in both directions, i.e. supporting corporate identities to consume external services as well as external identities to consume internal resources.
Quick Wrap Up
We’re just getting started on this topic.
Once you’ve made an assessment of existing identity stores, the next step is to define a transition architecture to position the Enterprise ready to harness existing and future investments, which is often harder to sell than you might imagine.
Today’s article was just to set the scene, the next article will step through the business case for establishing identity federation, and some of the excellent business value which can be realised from the exercise.