Intro
Windows 10 was officially released last week. In the wake of the release, concerns have surfaced about privacy and control issues which are enabled by default in all popular versions of the new Windows – including Enterprise edition. We’ll take a look at what reasonable steps you could (or should) make to your install.
First off, it is worth taking note of what edition you are running. Right clicking on the Start menu and selecting ‘System’ will yield the pertinent info:
Your edition of Windows 10
I am running Windows 10 Enterprise N, however most of what follows should apply to Pro and perhaps even Home edition.
Windows 10 Settings
Your first stop should be the Settings dialog. Note that if you’d prefer to import registry settings, jump to the bottom of this article.
This shouldn’t be confused with the traditional Control Panel. You can navigate easily here by clicking on the notifications icon in the system tray, or by right clicking on the Start menu and selecting ‘Settings’.
The Windows 10 Settings
We’ll look at the most important places from this menu.
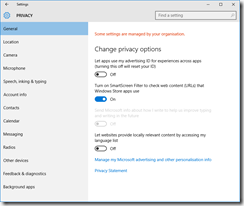
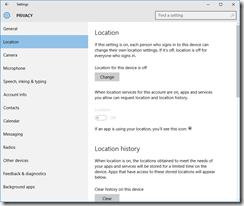
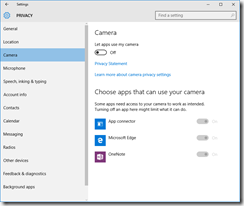
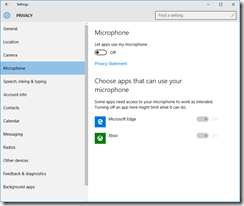
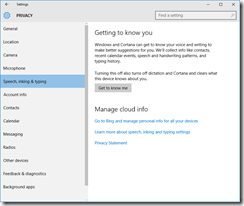
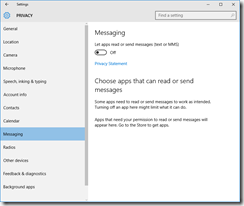
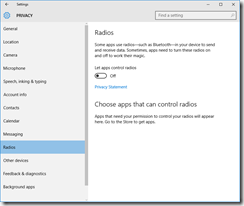
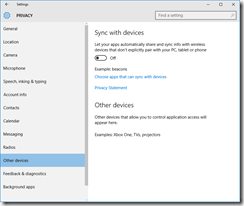
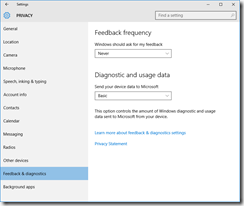
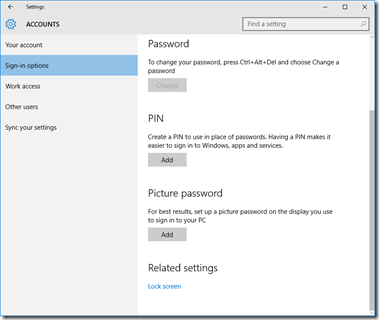
Privacy
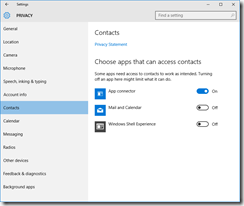
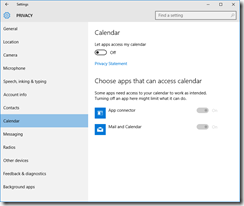
You’ll want to read carefully through each tab in the Privacy dashboard. I have taken screenshots of each one from the RTM build, showing what I’ve disabled. I don’t like sharing my personal info as a general rule, so I’ve been quite liberal in disabling mostly everything.
These are suggestions, you may or may not want some of the options enabled, depending on what apps and applications you are running.
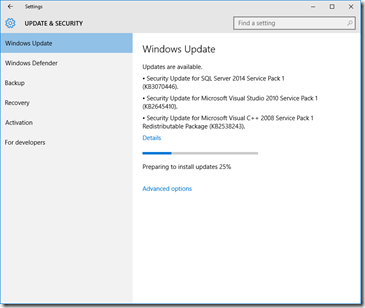
Updates & Security
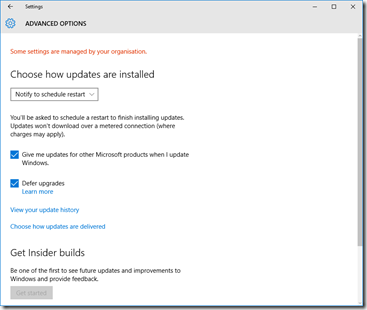
Some big things in this new version – the biggie being the Automatic download and installation of Windows Update patches, You might want to disable how you receive your updates, you can do this by going into the Advanced settings.
I’d recommend disabling some of these settings. They aren’t necessarily as nefarious as some have made out on the Internet, but there’s some value in taking some control over when and how your system updates. More on this in the Group Policy section, below.
Windows Defender
Unless you have a really good reason to do so, I DO NOT recommend disabling Windows Defender. However, there’s no harm in disabling the sharing of Defender information with Microsoft or others:
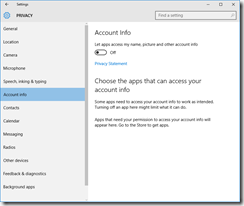
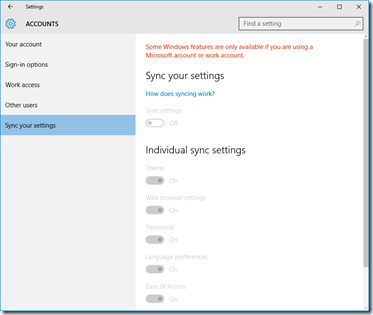
Accounts
If you use (or plan to use) a Microsoft Account, you might want to review what you share with the ‘Cloud’.
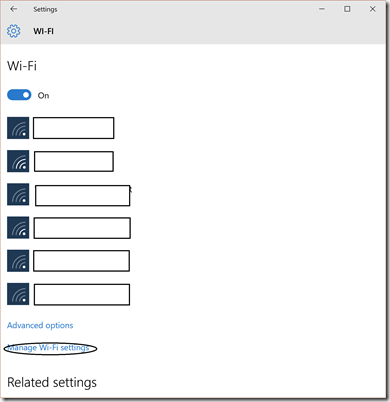
Network & Internet
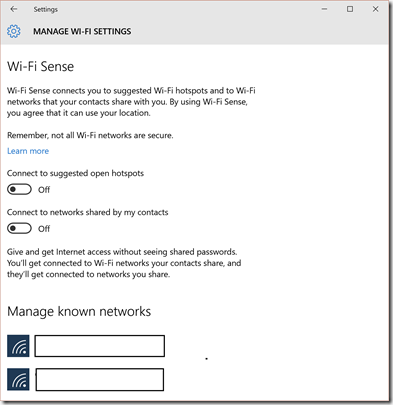
WiFi Settings – WiFi Sense
If you don’t want to inadvertently share your WiFi details with contacts, you may want to disable WiFi Sense. You do this through the Network & Internet settings.
Advanced
The next section requires a bit more work.
Group Policy
Policy is usually used by Network Administrators or Power Users to take more control over PCs. You’ll need to run the Group Policy Editor with elevated permissions (i.e as Administrator).
Here is the Group Policy Editor (gpedit.msc. Note that you can export to text file all the options. This is recommended if you want to free search for specific values.
Exported text
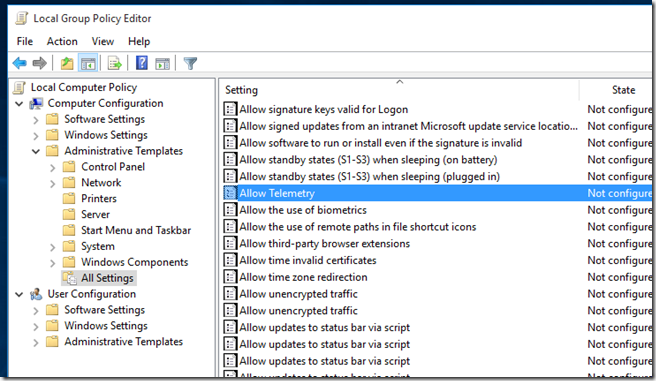
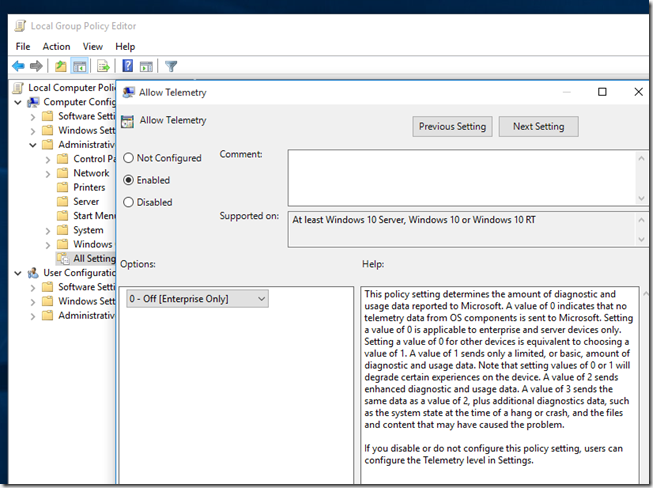
First off, why not use the policy to disable sending of diagnostic data (Windows Enterprise only):
Disable Telemetry (Sending Diagnostic Information)
Simply locate the “Allow telemetry” policy and enable, then set to zero (0) – applies to Enterprise edition only.
For non-Enterprise edition folks, you can try to disable Telemetry by modifying a registry value.
Open up the Registry Editor by launching regedit as an administrator. Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\DataCollection, select AllowTelemetry, change its value to 0, then apply.
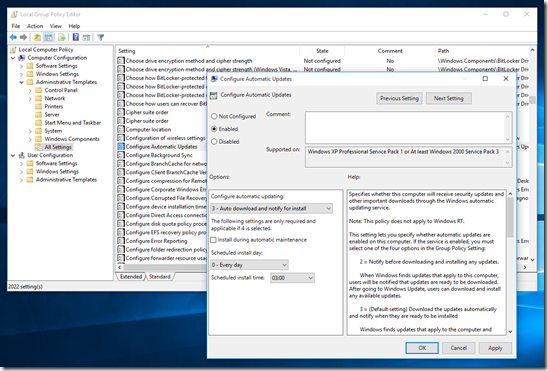
Disable auto-install of Windows Updates
[Updated: 06/08/2015]
I couldn’t verify that the group policies below were actually having any effect, so I took a look at previous registry settings instead. I’ll leave these policy bits in for reference, but you may want to try the registry option instead.
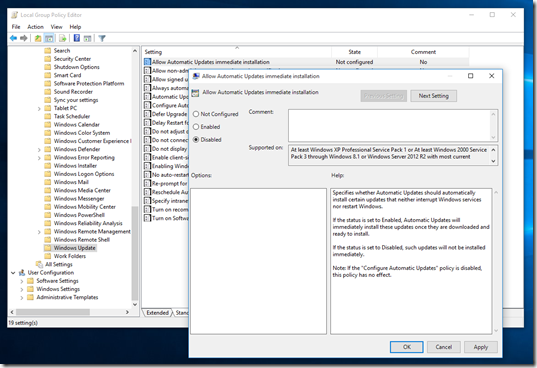
This one may or may not work, you need to ensure you have configured both “Configure Automatic Updates” and “Allow Automatic Updates immediate installation” policies:
Workaround – Registry
I took a look at previous OSes – particularly registry settings and then applied them to Windows 10 Pro and Enterprise editions.
Lo and behold, they abided by the settings!
Controlling Windows Updates with WSUS
Therefore, it stands to reason that if you operate a Windows Server Update Services (WSUS) server and you want Windows 10 clients to get updates from your WSUS server, you might want to apply this registry change. Windows 10 operating systems appear to WSUS as ‘Windows Vista’ (for Windows 10 Pro) or ‘Windows Vista Enterprise (N) Edition’ for Windows 10 Enterprise (N):
Computers running Windows 10 listed in the WSUS Computers list
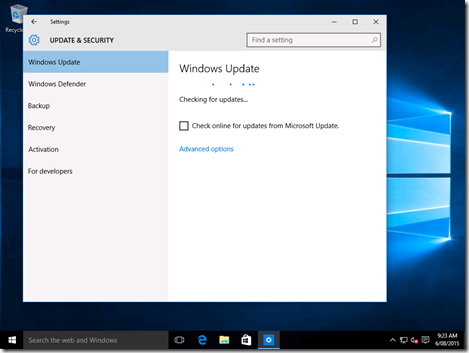
When configured successfully to use WSUS, there’s a slight change to the Windows 10 Windows Update settings page:
It stands to reason that you could omit the WSUS values to control how Windows Updates are applied. Here are the registry settings:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate]
“WUServer”=”http://<your WSUS server>:8530”
“WUStatusServer”=”http://<your WSUS server>:8530”
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU]
“NoAutoUpdate”=dword:00000000
“AUOptions”=dword:00000003
“ScheduledInstallDay”=dword:00000000
“ScheduledInstallTime”=dword:00000003
“UseWUServer”=dword:00000001
I located the possible values and meanings for the above settings via TechNet:
| Entry Name | Value Range and Meanings | Data Type |
| AUOptions | Range = 2|3|4|5 | Reg_DWORD |
| 2 = Notify before download. | ||
| 3 = Automatically download and notify of installation. |
||
| 4 = Automatic download and scheduled installation. (Only valid if values exist for ScheduledInstallDay and ScheduledInstallTime.) |
||
| 5 = Automatic Updates is required, but end users can configure it. |
||
| NoAutoUpdate | Range = 0|1 | Reg_DWORD |
| 0 = Enable Automatic Updates. | ||
| 1 = Disable Automatic Updates. | ||
| ScheduledInstallDay | Range = 0|1|2|3|4|5|6|7 | Reg_DWORD |
| 0 = Every day. | ||
| 1 through 7 = The days of the week from Sunday (1) to Saturday (7). |
||
| (Only valid if AUOptions equals 4.) |
||
| ScheduledInstallTime | Range = n; where n = the time of day in 24-hour format (0-23). |
Reg_DWORD |
| UseWUServer | The WUServer value is not respected unless this key is set. |
Reg_DWORD |
| AutoInstallMinorUpdates | Range = 0|1 | Reg_DWORD |
| 0 = Treat minor updates like other updates. |
||
| 1 = Silently install minor updates. |
For more information on these settings and what their values represent, check out TechNet.
Controlling Windows Updates without WSUS
If you do not use WSUS, try just setting these values in the registry:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU]
“NoAutoUpdate”=dword:00000000
“AUOptions”=dword:00000003
“ScheduledInstallDay”=dword:00000000
“ScheduledInstallTime”=dword:00000003
“UseWUServer”=dword:00000000
Disable Web Search from Start Menu
Finally, I found disabling the obligatory “desktop and web” search in the Start Menu significantly speeds up the Start Menu. Policy = “Do not allow web search”:
Cleanup: Remove Services
There are two key Windows Services which appear to participate in the sending of diagnostic data, Diagnostic Tracking Service “DiagTrack”and WAP Push Message Routing Service “dmwappushservice”.
Launch a Command Prompt as Administrator and execute the following:
sc delete DiagTrack
sc delete dmwappushservice
I haven’t noticed any ill-effects from removing these two Windows Services.
Registry Import
If you’d prefer to simply import that changes I made, copy this text and save it into a text file on your system (filename with a .reg extension) and import into the registry.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\default\Update]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\default\Update\AllowAutoUpdate]
“AllowedEnrollmentTypes”=hex(b):ff,ff,ff,ff,00,00,00,00
“HighRange”=dword:00000005
“LowRange”=dword:00000000
“MergeAlgorithm”=dword:00000001
“PolicyType”=dword:00000004
“value”=dword:00000002
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\default\Update\AllowNonMicrosoftSignedUpdate]
“AllowedEnrollmentTypes”=hex(b):ff,ff,ff,ff,00,00,00,00
“HighRange”=dword:00000001
“LowRange”=dword:00000000
“MergeAlgorithm”=dword:00000001
“PolicyType”=dword:00000004
“value”=dword:00000001
“WNFStateName1″=dword:a3bd3075
“WNFStateName2″=dword:13920028
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\default\Update\AllowUpdateService]
“AllowedEnrollmentTypes”=hex(b):ff,ff,ff,ff,00,00,00,00
“HighRange”=dword:00000001
“LowRange”=dword:00000000
“MergeAlgorithm”=dword:00000001
“PolicyType”=dword:00000004
“value”=dword:00000001
“WNFStateName1″=dword:a3bd2075
“WNFStateName2″=dword:13920028
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\default\Update\PhoneUpdateRestrictions]
“AllowedEnrollmentTypes”=hex(b):ff,ff,ff,ff,00,00,00,00
“HighRange”=dword:00000004
“LowRange”=dword:00000000
“MergeAlgorithm”=dword:00000001
“PolicyType”=dword:00000004
“PreCheckDLLPath”=”%SYSTEMROOT%\\system32\\PolicyManagerPrecheck.dll”
“value”=dword:00000004
“WNFNotificationMask”=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\default\Update\RequireDeferUpgrade]
“AllowedEnrollmentTypes”=hex(b):ff,ff,ff,ff,00,00,00,00
“HighRange”=dword:00000001
“LowRange”=dword:00000000
“MergeAlgorithm”=dword:00000003
“PolicyType”=dword:00000004
“value”=dword:00000000
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\default\Update\RequireUpdateApproval]
“AllowedEnrollmentTypes”=hex(b):ff,ff,ff,ff,00,00,00,00
“HighRange”=dword:00000001
“LowRange”=dword:00000000
“MergeAlgorithm”=dword:00000002
“PolicyType”=dword:00000004
“value”=dword:00000000
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\default\Update\ScheduledInstallDay]
“AllowedEnrollmentTypes”=hex(b):ff,ff,ff,ff,00,00,00,00
“HighRange”=dword:00000007
“LowRange”=dword:00000000
“MergeAlgorithm”=dword:00000001
“PolicyType”=dword:00000004
“value”=dword:00000000
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\default\Update\ScheduledInstallTime]
“AllowedEnrollmentTypes”=hex(b):ff,ff,ff,ff,00,00,00,00
“HighRange”=dword:00000017
“LowRange”=dword:00000000
“MergeAlgorithm”=dword:00000001
“PolicyType”=dword:00000004
“value”=dword:00000003
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\default\Update\UpdateServiceUrl]
“AllowedEnrollmentTypes”=hex(b):ff,ff,ff,ff,00,00,00,00
“MergeAlgorithm”=dword:00000003
“PolicyType”=dword:00000001
“value”=”CorpWSUS”
“WNFStateName1″=dword:a3bd2875
“WNFStateName2″=dword:13920028
Inspiration(s)
The following links were helpful in compiling this article
https://www.reddit.com/r/Windows10/comments/3f38ed/guide_how_to_disable_data_logging_in_w10/















One thought on “Privacy in Windows 10”
Hi,
Can you please explain what these configurations are?
“AllowedEnrollmentTypes”=hex(b):ff,ff,ff,ff,00,00,00,00
“HighRange”=dword:00000007
“LowRange”=dword:00000000
“MergeAlgorithm”=dword:00000001
“PolicyType”=dword:00000004
“value”=dword:00000000
I have worked with the registry briefly, adding keys and setting values, but I have never used these keys before. If you could give me some insight or resources I would greatly appreciate it!
Thanks,
Luke