Windows Server 2016 was launched less than two months ago, and one of the attractive options is an excellent makeover of Active Directory Federation Services (AD FS).
The latest version is stacked with great features and is seriously worth the upgrade. However, I thought I’d point out one of the best “low hanging fruit” features which is a no brainer to enable, and quite useful.
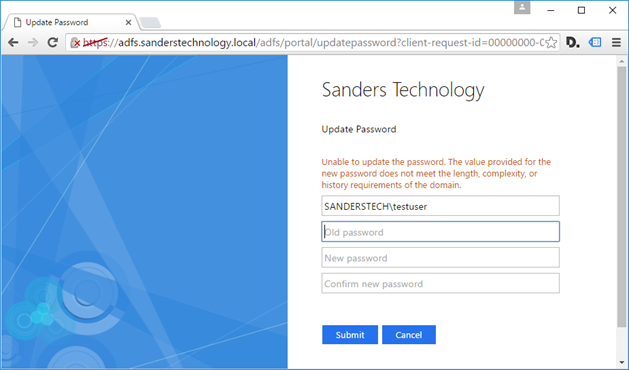
The new version (as the previous version does) supports web based functionality to handle the reset/changing of domain user accounts. This is simply brilliant, as it avoids the need for custom code, or for users to logon interactively with domain machines to change their passwords.
The scenarios for this functionality are:
- Expired Password: User is accessing applications such as Office 365 and is logging onto ADFS using their expired password. At this time, ADFS will interrupt the login flow (when password change is enabled) and ask the user to change their password. Once they change their password, they are seamlessly taken back to the login page, enter their changed password and subsequently taken to the application that they were logging into.
- User Must Set Password at next login: Many times when you have a new employee or when a password is reset through a password reset mechanism such as the SSPR feature in Azure AD, users need to change their passwords at the next login into AD.
- Change Password when passwords are soon to expire: We targeted this case specifically for Office 365 applications where ADFS can notify Office apps that a password is set to expire with 14 days (not configurable) and notify the user and now the user can just click on the change password link when this notification appears and can change their password via ADFS.
- Change Password any time by directly going to the password change URL: This is simply a case where the user can bookmark the change password URL and just access this to change their password in AD.
Update Password
To enable this portal functionality is child’s play. Once you have installed the AD FS role on a fresh copy of Windows Server 2016, you’ll need to make a small modification to the configuration. Open the AD FS Management console:
Once loaded, expand the left hand navigation and click on the Endpoints folder:
In the main window, scroll to the bottom or look for the HTTP transport Type (there should only be one).
Click on Enable on the far right hand side action panel.
Restart the federation service, and you’re done.
Domain users can now change their passwords via a browser, completely out of the box.
Naturally, I believe you’ll be able to skin this page and modify the text as per previous versions, but I haven’t looked at the latest version just yet.
The server will nicely log any errors, just in case:









4 thoughts on “Windows Server 2016/AD FS – Update Password”
Hello,
I enabled password update and the website works however if a user tries to login to O365 with an expired password or an account set to change password on login they just keep failing ADFS auth instead of being directed to the change password site. Any ideas?
Hmm, I suspect that the update password is only mean for when ADFS is proxying for an on premise Active Directory. O365 likely has a far more advanced interface (including 2FA) although I think it’d be fair to get redirected to the O365 password management portal when the account is an O365 account. Might be worth trying on ADFS 4 (Win Server 2016) if you’re on Win Server 2012 R2?
Is there any way to handle the password reset via code? We are gathering the Username and Password and doing silent authentication. Should the AD password be changed we would like to handle this outside of ADFS UI so that we can gather the new password entered by the user.
Not with AD FS natively (as of v3 it’s a closed application, only client side scripting is supported), but you could roll your own code (I have done in the past) wrapping the .NET Framework’s ‘implementation’ of AD support (COM-based LDAP/S). Debugging it is a PITA as you have to go native to see the actual COM exceptions when issues arise (e.g. gpo issues etc) the framework tends to swallow the detail and give you a generic error in managed land.